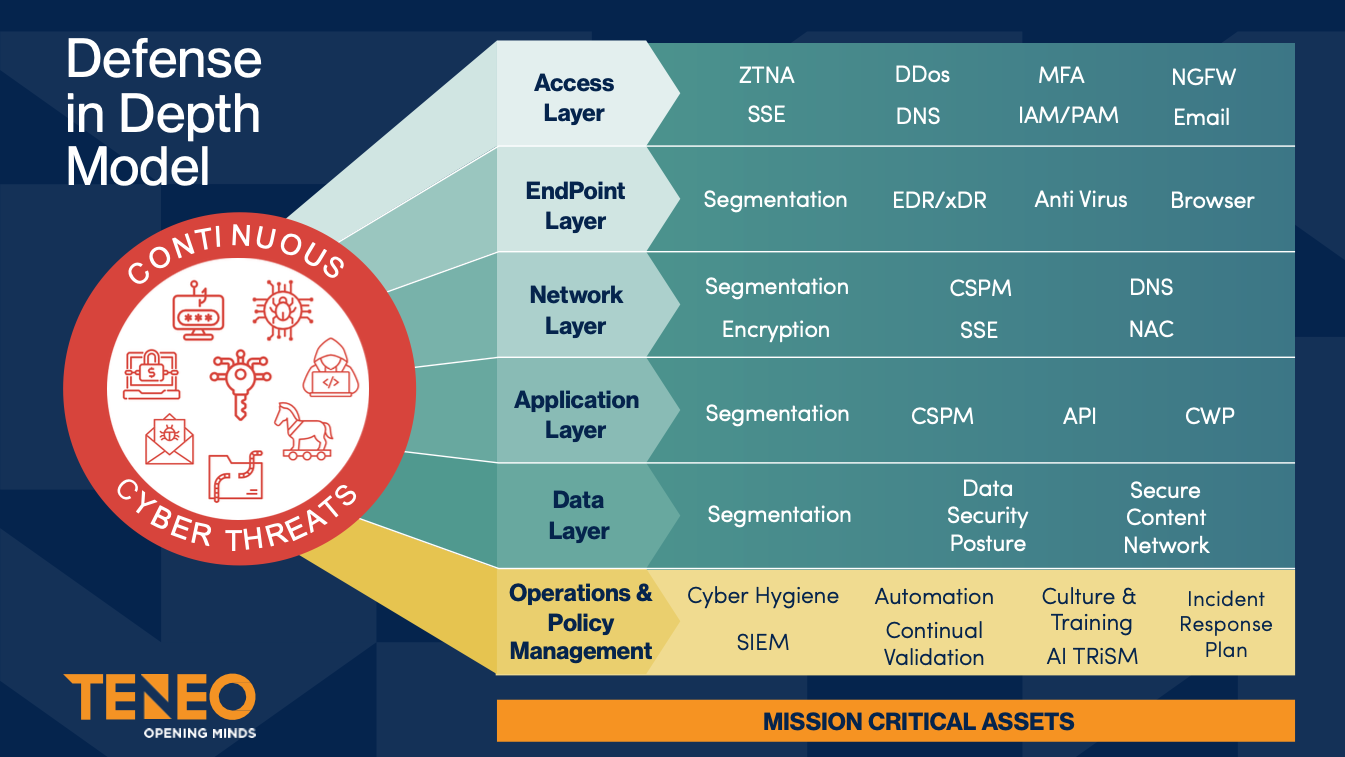
Making the case
As organizations continue to expand their networks, integrate remote workforces, and deploy new applications, cybersecurity threats are evolving at an unprecedented pace. Traditional perimeter-based security approaches are no longer sufficient to safeguard digital assets. To effectively mitigate these risks, businesses must adopt a Defense-in-Depth strategy, which leverages multiple layers of security controls to provide proactive and resilient protection.
The modern threat landscape presents several critical challenges. Perimeterless environments, driven by cloud adoption, IoT devices, and hybrid work models, have introduced new security blind spots. The attack surface continues to grow, as businesses rapidly integrate new applications and services, increasing the number of potential vulnerabilities. Evolving cyber threats, including ransomware, phishing, and zero-day exploits, necessitate advanced defense mechanisms. Additionally, organizations must ensure regulatory compliance with frameworks such as GDPR, ISO 27001, and NIST to avoid legal and financial repercussions.
A robust cybersecurity framework incorporates multiple protective layers. Network security measures such as firewalls, IDS/IPS, and micro-segmentation to safeguard traffic flow. Endpoint protection solutions, including xDR, and Email Security, secure user devices from threats. Identity and access control mechanisms like MFA, zero trust, and RBAC prevent unauthorized access. Data security strategies such as encryption, DLP, and regular backups ensure the integrity of sensitive information.
Application security practices, including WAF, API protection, and secure coding, help prevent exploitation. Threat detection and response tools like SIEM, threat intelligence, and automated response systems provide continuous monitoring and remediation. Lastly, user training programs and phishing simulations reinforce security awareness and reduce human risk.
With our Defense-in-Depth Model, Teneo aims to streamline adoption of this approach. Whether your environment is well on its journey to better security to meet the threats of tomorrow or you’re in the early stages of taking your first steps on the journey, our versatile framework and experienced resources adapt to address your key challenges and exemplify your strengths throughout the entire process.